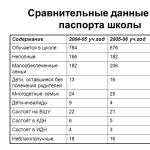
Failures arising from the operation of storage media on hard drives can be caused by many reasons, including manufacturing defects. In this article, we will consider the nature of failures caused by external mechanical influences on the hard drive (shocks, concussions, shocks, since they are the "invisible" provocateurs of the death of a hard drive in 53% of cases), as well as technologies implemented in the latest modifications of hard drives. disks in order to significantly increase the resistance of media to these influences.
Any failure or malfunction in the drive can result in partial or complete loss of very important and sometimes invaluable information. In view of the fact that a significant proportion of malfunctions in drives is the result of mechanical influences not envisaged by the specifications, nowadays special attention has been paid to protecting the HDD from shocks and shocks.
Impact and its consequences
Falling a hard drive (even from a very low height) can cause internal damage to the drive, despite the fact that the outside of the hard drive case looks flawless, and there are no traces of mechanical impact on it. The safest such impact will be if the HDD failure or the presence of errors on it were detected during testing at the manufacturer's factory. In this case, the drive is discarded and on this its life path is over. This is not scary, since it will never go into operation and information will never be recorded on it. It is much worse if the malfunctions that arose during testing did not manifest themselves in any way, and the drive went on sale. Such malfunctions are dangerous in that they will manifest themselves later, gradually deteriorating the parameters of the drive, they pose a threat to the data stored on the drive ...
Hard drives are most vulnerable to mechanical shock when removed from the original manufacturer's packaging, which is specifically designed to protect the drive after it has left the factory. A hard drive installed in a computer case is more protected from external influences, since in most cases the PC case absorbs shock energy, and the degree of impact on the hard drive can be significantly reduced. Therefore, it is necessary to distinguish between non-working and working shock resistance of drives.
- Impact is a sharp and strong mechanical impact on an object characterized by a very short duration. Impacts are characterized by huge accelerations that an object receives in a very short time. Therefore, the level of shock to which the object was subjected is usually measured in units of multiples of the acceleration due to gravity G, equal to 9.8 ms2.
- The shock resistance of a drive determines its ability to withstand the specified values of accelerations obtained during an impact for a certain time. The standard time of impact on drives is considered to be 2 milliseconds..
- Operating shock resistance determines its resistance to shock in working condition, which ensures the error-free writing / reading. The operating shock resistance is usually not great and is about 10-15G for old drives and up to 70-150 for the newest ones assembled using protection technologies. Fortunately, drives in a working system are very rarely hit, and the energy of these impacts is significantly reduced by the structural elements of the computer case, so hard drives rarely get damaged in this state..
- Disconnected shock resistance determines its resistance to shock in the inoperative (disconnected) state in which the drive does not suffer internal damage. This is a very critical characteristic, since a drive in 95% of cases receives shock mechanical damage exactly at those moments when it is outside the computer case. Shocks received in these cases can amount to hundreds of Gs in a time of 1-2 milliseconds..
Most often, hard drives experience shock during transportation from the supplier to the consumer and during the process of their installation in a PC by insufficiently qualified or ill-informed personnel. In Russia, the situation is often aggravated by the fact that batches of hard drives are transported unprepared for this transport, without providing any additional protection measures in the event of a car collision or just sudden braking. Very often firms - sellers of components, when selling hard drives, transfer them to the buyer packed in a single electrostatic shell. But the buyer has to take it to the house or to work. And where is the guarantee that the seller himself did not knock this screw, and this is very likely in such points of sale as radio markets. It is enough to see how they are treated there. Moreover, a hard drive can experience a sufficiently strong impact if you accidentally poke it with an assembly tool, for example, a screwdriver, bump two hard drives together or as a result of pushing the hard drive into its seat in the computer case ... Figure 1 shows the most typical cases of shock impacts on hard drives and the degree of their impact on hard drives. Vertical - impact force in multiples of gravitational acceleration (G), horizontal impact duration.
The most detrimental are shocks with high energy strength and short duration of impact, usually hundreds of Gs in less than one millisecond. These shocks are grouped in the upper left corner of the figure and are usually outside the shock resistance of standard drives. Typical consequences of these blows are most often:
- slap heads;
- slippage and displacement of discs in the package;
- the appearance of play in the bearings.
The most common consequence of an impact in a storage device is a “head slap”, Figure 2. It occurs when the impact energy is directed vertically or at an angle to the horizontal plane. In this case, there is a separation of the magnetic head from the surface of the disk and then its sharp drop on the surface of the magnetic disk. At the moment of contact, the head cuts into the surface with its edge, the position of the head is leveled and it is forcefully pressed against the surface by the entire plane. As a result, the disk receives surface damage, the smallest particles and debris are scattered over the surface of the magnetic disk.

Do not think that these fragments will be able to fly away from the disk due to the centrifugal forces arising from the frantic rotation of the disk. Due to the magnetic nature of the disk and the microscopic size of the debris, they remain on the disk and cannot be removed from there. In addition, after the impact, the head itself may be physically damaged, and its magnetic properties deteriorate sharply. In practice, these damages appear in the form of so-called "broken clusters". If you view such a disk in programs with a visual interface such as Norton Speed Disk, then surface damage will appear in the form of one or more chaotically located bad clusters. Damage caused by a defect in one of the heads will most likely manifest itself in the form of a much larger number of defective clusters and some pattern will be clearly traced in their location. But even if the defects on the disk did not appear immediately after the shock impact on the drive, these defects will make themselves felt later (in a month or even a year!). Why? Let's consider this issue in more detail.
Magnetic resistive heads and their work
The principle of operation of a magneto-resistive (MR) head when reading data is to change the resistance to electric current in accordance with the change magnetic field... The reading element of such a head is a very thin film of a special material, which changes its resistance in accordance with the arrangement of magnetic domains on the surface of the rotating disk. The location of these domains is determined by the information written to disk. The change in the resistance of the film is recorded by a special reading channel and is transferred for further processing to the comparator, which finally determines what was written, zero or one. MR heads have another property that is directly related to our topic - the final active resistance of the film depends on its temperature.
Under normal conditions, when the disc is unrolled to the working speed, the air flow raises the head above the disc, and it hovers over the smooth surface of the disc without touching it. If on the disk there are particles or irregularities comparable in size to the gap between the head and the disk, then they, sweeping with great speed under the soaring head, touch it, and friction instantly heats the head. This heating immediately affects the resistance of the film coating of the head and it rises sharply. The read channel misinterprets the change in head resistance and it becomes impossible to read data in this place.
Constant exposure to temperature prematurely ages the head, and particles passing under the head act like an abrasive cloth. The ability of the head to respond to changes in the magnetic field deteriorates over time (more and more unreadable sectors appear on the disk, or, as they say, the disk began to "crumble"), and eventually a complete failure of the head occurs.
Decision
One of the possible solutions to the problem may be the caution and skill of people handling drives. But it is difficult to solve the problem in this way, because even abroad, more than 30% of hard drives are installed in computers by untrained personnel outside of computer manufacturers. In Russia, this percentage is much higher. Moreover, there are many cases where shock effects are the result of accident, and not negligence.
Thus, the solution to this problem should be realized through an increase in the shock resistance of the drive itself. IN Lately drive manufacturers have developed a range of low-cost and effective technology solutions to improve shock resistance and product reliability, and fortunately, now this solution is not limited to the "Handle with care!" on the case.
Let's see what the main manufacturers offer us.
Quantum
SPS technology
SPS (Shock Protection System) technology was developed in the first half of 1998 and was first introduced in the Fireball EL series hard drives. It represents 14 improvements and technological solutions in the drive design aimed primarily at absorbing and minimizing the negative effect of high-energy shocks and short time impact. This was the result of a long and careful study of the behavior, interaction of structural elements, loads and their distribution during impact. Again, the most detrimental consequence of such blows is the separation of the head from the disk and its further sharp slap on it. Solutions applied by Quantum engineers eliminate or significantly reduce the head lift-off height upon impact (Figure 3). Most of the impact energy is absorbed by the rest of the drive's structures, which prevents spanking and debris from causing premature aging of the hard drive. On the currently, the following Quantum models are built using SPS: VikingII, Fireball EL, Fireball CX, Fireball CR, Fireball Plus KA, Fireball Plus KX, Atlas III, Atlas IV, Atlas 10k, BigFoot TS.

SPS II technology
SPS II technology was a logical continuation of SPS technology and was announced in 1999. The first hard disk with such technology was Fireball Ict. While SPS provided an increased level of resistance to shocks received by a drive in an inoperative state, SPS II additionally protects a working drive from writing / reading at moments of shock and shaking that occurs in case of jolts of the system unit working computer. Instead of being written to disk, the data is cached and will be written to disk later when the shock energy has been consumed and the disk is at rest. Figures 4 and 5 show the process of recording at the moment of impact on unprotected and protected by SPS II technology. At the time of writing, SPS II is used in three latest models Quantum - Fireball Ict, Fireball Ict10k and AtlasV.

Figure 4: Writing to a disc without SPS II technology

Figure 5: Writing to a disc with SPS II technology during impact
Seagate
GFP technology

Seagate's G-force protection (GFP) technology combines a number of technology solutions to improve the non-operational shock resistance of media. This technology provides a greater degree of protection for hard drive components such as the drive motor and bearing, heads, flexible head holders, and discs.

By reducing the mass and size of the heads, as well as increasing the clearance between the holder and the disc, the company's engineers have significantly reduced the kinetic energy of these components acquired during the impact process. This means that the heads have less chances to make a slap on the disc at the time of external influence. Seagate has also paid attention to the protection and strength of the disc pivot bearings and the disc carrier in the package.
Defects occurring in the bearing (see Fig. 6) lead to increased noise and vibration of the hard drive, which can ultimately lead to engine failure.
Slippage of disks in the mount is quite rare, but even if it happened as a result of an impact, the hard drives of the Barracuda and Cheetah families have always had the ability to work with a slipped disk thanks to the built-in head correction system for each disk revolution (once per revolution compensation - OPR) ... The disc servo system uses OPR to determine how much the disc has been displaced from its original position and adjusts the position of the heads accordingly so that the position of the head matches the track recorded on the disc. The GPS technology uses an improved OPR system that doubles the servo's ability to handle shifted discs.
The GPS technology will be applied to the latest high-performance Seagate Barracuda 18LP / 36/50 and Cheetah 18LP / 36 drives. In general, the use of GPS will allow, according to the manufacturer, to increase shock resistance by 30% for Barracuda drives and 40% for the Cheetah family.
Maxtor
Maxtor also did not stand aside, and developed its own technology called ShockBlock. The first drive with this technology was the DiamondMax Plus 5120. As with competing technologies, the head slap problem is solved by reducing the physical size and weight of the head. But here Maxtor has added another solution. We all know that in a non-working state, the hard drive heads are located in the so-called landing zone, in the zone where information is never recorded. Therefore, by strengthening the coating of the magnetic disk in the landing zone, the company significantly reduced the likelihood of the appearance of small particles and debris in the case when the head nevertheless hit the drive in a disconnected state.A further development of this technology was the ShockBlock Enhanced technology. Now Maxtor claims that its technology allows its drives to withstand shocks up to 1000 G !. The first drive produced with this technology was the DiamondMax 6800. Why such high shock resistance was achieved. According to Maxtor, by making the head holders more flexible, manufacturers not only do not reduce the force of the head slap against the disc, but even increase it, since the "whip" effect only increases the impact. Maxtor, on the other hand, has made the holders much more resilient in their new drives. Inevitably, by increasing the elasticity of the holder, the company had to additionally solve the issue of ensuring the previous "hover" of the heads over the disc during its rotation. And apparently she succeeded. Moreover, the company has gone further. Having just reasoned that the detrimental effect is not so much the spank itself, but its consequences (particles and debris on the disk), then it is necessary to make sure that even after the spank the appearance of splinters is less likely. Take a look at the picture. The head, lowering after the impact, always hits the disc with its edge. The chances of damaging the disc are very high.

Therefore, the company changed the design of attaching the head to the holder in such a way that even during a slap, the head would hit the disc evenly with its entire surface. This several times reduces the likelihood of the appearance of fragments and particles after the impact of the head.

Fujitsu
The company has not invented or patented any high-profile technology to protect drives from shock, but, nevertheless, many of the hard drives currently produced are very resistant to non-operational shock loads. For example, hard drives of the MPE3xxx series have shock resistance at the level of 250 G. And models of the Hornet 9, 10, 11 series up to 600 G! Moreover, their variants for mobile computers are capable of normally carrying up to 700 G in an idle state and up to 125 G during operation.
Samsung
In the first quarter of 2000, Samsung will present in Russia two new models of SpinPoint series hard drives: V9100 and V10200. The combined use of two proprietary impact protection technologies ImpacGuard (TM) and Shock Skin Bumper (TM) in these models will provide protection against shock effects up to 250G when inoperative. Earlier SpinPoint models of the V6800, V4300, V4, V3, V3A, V3200 series have 75G ratings for 11 ms exposure time (or 200G Ref. For 2ms exposure duration). The model of the W2100 series, in which these figures are lower, falls out somewhat from this row.
Western digital
I could not find any information about the special shock protection technologies used in the hard drives of this company. But, judging by the technical data of the hard drives, these technologies may not have existed. A number of models launched into production recently have increased shock resistance at the level of 150-200 G. The rest of the models are at the level of 60-70 G. Therefore, they also require very gentle handling.
IBM
The currently existing DeskStar and UltraStar series drives with a capacity of over 3.5 Gb have a shock resistance of 175 G when not in use. Models in these series with capacities below 3.5 Gb have less ability to withstand external shock. Models of hard drives for mobile computers of the TravelStar series from 2.2 Gb and above have very good performance and are capable of carrying up to 400-500G in an idle state and up to 150 G in a working one. The recently announced new models of UltraStar 36, 72 hard drives will be produced using Active Damping technology, which will allow these drives to be used in conditions with high vibration levels.
Conclusion
A hard disk is a very sensitive device to shocks and shocks and therefore requires very careful attention. Discs produced a year and a half ago had very little shock resistance (at the level of 60-100G), so some of you, probably, only now see on your "screw" the results of a blow made a year ago, which you did not even suspect.
Having bought a hard drive, pay attention to the failed clusters that appear during the warranty period, and if at least one appears, change it immediately. And do not fall for any salesperson's beliefs that one or two unreadable clusters are within the normal range. The appearance of broken clusters will inevitably lead to the emergence of new and new ones, up to the failure of the hard drive. The only question is how long it will last.
In preparing the article, materials and technical documentation from manufacturers' websites were used
How to password protect an external hard drive
What should you do to protect external media yourself with a password?
Data protection on such devices is permissible using special utilities. After searching the Internet, I found that TrueCrypt, Folder Guard, Disk Password Protection, and Cryptainer + DecypherIT turned out to be the most efficient and easy ones. Finding and downloading them is easy. My task is to explain to you * how to protect an external hard drive with a password * after installing these utilities.
It is best to leave the external hard drive empty before the process. So it is faster to work with it and there will be no fear of data loss in the event of your erroneous actions. If you need to password protect the device with data, I advise you to copy them to your computer.
Now let's look at the use of each of the utilities in more detail.
TrueCrypt
What do we do:
1) launch TrueCrypt;
2) click "Create volume";
3) select "Encrypt non-system partition", click further;
4) select "Normal volume", then further;
5) press the button "Device ...", find and click our device and press ok;
6) after that the Volume creation mode window will open. We select the first item if we have cleared or copied our information to another medium. If they did not take care of this, we select the second item and wait a longer time than in the first case;
7) in the encryption settings window, leave everything as it is and click next;
8) now we indicate a cipher of 20 characters and symbols;
9) the Format Volume window appears. To File. sist. select NTFS, do not change the rest and click Markup;
10) encryption has started. The completion time depends on the size of the drive and the availability of data on it. So a blank external 1 TB disk is processed for more than an hour;
11) upon completion, press ok and exit. We are thrown into the main menu, where you need to assign a free letter to the volume and then select our disk;
12) ok / mount / code / ok.
That's all - the device was able to be protected with a password.
Folder Guard
 After its launch, a window appears in which the connected devices are visible. Click on your connected media with the left mouse button and proceed to install the cipher. It's pretty simple. Press the left mouse button "Lock with a password" and enter the invented numbers, symbols in the top line. And at the bottom we repeat them. Then we confirm by clicking ok in the subsequent windows. At the end you will be asked to save your settings. You save them and close everything.
After its launch, a window appears in which the connected devices are visible. Click on your connected media with the left mouse button and proceed to install the cipher. It's pretty simple. Press the left mouse button "Lock with a password" and enter the invented numbers, symbols in the top line. And at the bottom we repeat them. Then we confirm by clicking ok in the subsequent windows. At the end you will be asked to save your settings. You save them and close everything.
Further, when you try to open the hard drive, you will be prompted to enter the code. And when you close it, a window pops up asking whether to keep it classified. If you leave, then you will enter the code every time you open it. If not, then the hard drive will again be in the public domain, and in order to password protect it, you will have to go through the procedure again.
Cryptainer + DecypherIT
 As usual, launch the installed Cryptainer. We see tooltips in the windows where they ask to enter the parameters for encryption. We do whatever is asked. We indicate the location of the encrypted device, its size and password. Next, we get acquainted with the usefulness of the program that appears in new windows and tells * how to password-protect an external hdd * yourself. Then we indicate the path to our disk and click Load.
As usual, launch the installed Cryptainer. We see tooltips in the windows where they ask to enter the parameters for encryption. We do whatever is asked. We indicate the location of the encrypted device, its size and password. Next, we get acquainted with the usefulness of the program that appears in new windows and tells * how to password-protect an external hdd * yourself. Then we indicate the path to our disk and click Load.
So we encrypted external media... With this utility, you can password-protect anything, even separately: sound, video, text files, etc.
In the absence of the Cryptainer program, you need the DecypherIT utility and your previously entered secret code to view the data.
Disk Password Protection.
 Like the previous utilities, we also install this on our computer and run it. In the window that opens, select what we want to hide from not the right people and launch the "Protection Wizard" by checking the "Master" and "Protection". Then we indicate the type of protected hard disk and continue by clicking "Next".
Like the previous utilities, we also install this on our computer and run it. In the window that opens, select what we want to hide from not the right people and launch the "Protection Wizard" by checking the "Master" and "Protection". Then we indicate the type of protected hard disk and continue by clicking "Next".
The following actions must be performed in accordance with the requests that appear in the new windows. After that, in a special form, you need to indicate the invented complex code and confirm it by redialing it in another line.
The program also makes it possible to set a hidden protection mode. To do this, after entering the password, check the box for this mode and click "Next". The last step and everything is protected from outsiders.
Personal opinion
If for you these programs seem too abstruse and are already tired of searching, downloading and installing many utilities for encryption, I offer an alternative to your suffering - hdd with built-in encryption. He does everything himself: encrypts and decrypts data. And you don't need to install anything extra. However, there are also downsides. If the controller or other electronics fail, there will be no chance to transfer data from the device to another medium.
Set a password on your external hard drive- this is the right thing. All information must be personal and not used by anyone. So you are on the right track. Choose the program you like and protect your data. Just do not forget to write down the password you have invented somewhere. Memory can sometimes fail and everything will not be available even for you.
The confidentiality of data stored on disk drives of computers is one of the most important conditions for the functioning of most organizations, both large and small, and is one of the most important components of the personal safety of individual citizens. It is the problem of ensuring the security of user data that the system of passwords installed on disk drives solves. General order the functioning of passwords is described by the ATA standards, although each disk manufacturer can make its own peculiarities in the password system. This article will help you understand all the nuances of disk passwords.
The most common ways to restrict access to confidential information stored on a disk are:
- creating encrypted partitions on the disk;
- archiving with a password;
- setting a password on the file system at the logical level (by special programs in the boot sector of the HDD);
- physical change of the entire hard disk (using the mobile rack).
But each of these methods has its own drawback. The information still remains on the medium, and although it is not explicitly available (protection programs are often limited to encrypting only the boot record, leaving even FAT unchanged), it can be easily extracted from such a disk using disk editors or information recovery programs, for example , Easy Recovery.
On-the-fly file encryption is more resistant to cracking, but its operation requires a resident resident in memory, intercepting part of the system API and creating a considerable load on the central processor. In addition, such a program may crash and freeze, which creates a number of problems. Also, do not discount the possibility of damage to the encrypted partition, for example, by viruses. All this leads to significant difficulties in the subsequent extraction of information.
The security system for user data must meet three basic requirements.
1) First, the security system must be independent of the operating and file system.
2) Secondly, the security system must be reliable and it must be very difficult to break into it.
3) Third, the security system should not take away the computing resources of the system.
Since the adoption of ATA / ATAPI-3 in 1996, information protection can be carried out by means and forces of a hard disk controller. The security system - Security Set or Security Mode - allows you to protect the entire contents of the disk not only from reading, but also from writing, and even from low-level formatting. This was achieved by integrating the protection program directly into the disk drive. This program is controlled by several special commands sent to the disk via the IDE interface using the appropriate utilities. In addition, the BIOS "s of some motherboards allow you to set passwords on modern hard drives. The security system is especially relevant for laptops, in which the presence of disk passwords is, in fact, mandatory.
Safety system
In accordance with the ATA / ATAPI standards (in particular, when writing this article, we will rely on ATA / ATAPI-8), the disk security system is optional, i.e. is used exclusively at the request of the user. The security system allows you to manage passwords that restrict access to data stored on the disk. The ATA standard describes two types of passwords:
- User Password
- Master Password (administrator password).
In addition, the standard describes two levels of security:
-High (high);
- Maximum.
A disk device that is equipped with a security system must support at least the following commands:
- SECURITY SET PASSWORD (command for setting User-password);
- SECURITY UNLOCK (command to unlock when entering the correct User-password);
- SECURITY ERASE PREPARE (command for preparing data for destruction);
- SECUTITY ERASE UNIT (command to destroy data);
-SECURITY FREEZE LOCK (command to pause disk lock);
-SECURUTY DISABLE PASSWORD (command for canceling the security system, i.e. canceling the User password).
The ability of the disk drive to support the security system and its current state are reflected in the data block (identification block - passport) obtained using the IDENTIFY DEVICE command. In this data block, two words correspond to the security system:
- word with address 82 (the presence of this word is mandatory in the data block);
- word with address 128 (the presence of this word in the data block is optional).
If [bit 1] of the word with address 82 is set to logic 1, then the disk drive supports the security system, and if this bit is set to logic 0, then the use of the User password is impossible. Word with address 128 describes the current state of the security system and its format is presented in Table 1.
Table 1.
|
Bit |
Appointment |
|
0 |
If the bit is set to log 1, then the disk supports the security system. The state of this bit is not changed. |
|
1 |
If the bit is set to log 1, then the security system is enabled. |
|
2 |
If the bit is set to log 1 LOCK (locked until password is entered). |
|
3 |
If the bit is set to log 1, then the disk is in the state FROZEN (password is "frozen") |
|
4 |
The bit is set to log 1 when the password attempts counter has exceeded the allowed value (5 attempts). |
|
5 |
If the bit is set to log 1, then "extended cleanup" is supported by the disk. The state of this bit is not changed. |
|
6-7 |
Bits are reserved |
|
8 |
Security level bit. If the bit is set to log 1 Maxi - mum ... If the bit is set to log 0, then the protection level is set High. |
|
9-15 |
Bits are reserved |
Consider the features of passwords and security levels.
User password
User-password is used to restrict access to user information. When a User password is set, the hard drive enters the LOCK state and rejects commands such as reading and writing. Therefore, information from a password-protected disk can neither be read, nor changed, nor erased. This can be done only after removing the password or after temporarily unlocking the disk. When setting the User-password, the security level is set (High or Maximum), i.e. the security level is a parameter of the command that sets the User password. The security level determines how the hard drive will react to entering the Master password. The disk security system is activated only after the User-password is sent to the hard drive using the SECURITY SET PASSWORD command.
Master password
The master password is a unique code that is stored in the service area of the drive, sometimes in encrypted form. The master password is not intended to protect information. Master-password is designed to delete User-password in case of loss of the latter. The master password cannot be used to lock or unlock the drive. The master password can only be changed. Setting the Master password does not affect the operation of the drive in any way. The master password is set at the disk manufacturer, and, in principle, the master passwords of the major HDD manufacturers are known.
Security level High
A drive locked with a High security level can be unlocked using either the Master password or User password. Therefore, when protecting a disk, it should be borne in mind that if the Master password was not changed in a timely manner, then unlocking a drive with a High protection level is not difficult. To unlock a disk in High mode, use the SECURITY UNLOCK command, which sends the Master password to the disk.
Security level Maximum
When you set the protection level to Maximum, you can unlock the drive only if you know the User password. If the User-password is unknown, but the Master-password is known, then the drive can be unlocked only with the simultaneous destruction of all data. If the security level is set to Maximum, then the SECURITY ERASE PREPARE and SECURITY ERASE UNIT commands, in which the Master password is specified, are used to unlock the drive with the Master password.
A graphical representation of the principle of unlocking a disk using a User-password and Master-password is presented on fig. 1.
Fig. one
Once again, we draw the readers' attention to the fact that the Master password is not some kind of "universal master key", but allows you to unlock the drive only under a certain set of circumstances (when the User password is unknown, but the protection level is set to High).
If neither the User-password nor the Master-password is known, then the protected disk becomes physically unusable for storing information. Without knowing the Master password, it is practically impossible to unlock the disk, even at the cost of lost data (although, under certain conditions, the password, if it is not encrypted, can be read from the disk surface using technological commands). Therefore, working with the HDD security system requires both the user and the service specialist to be extremely attentive and careful.
After the security system is activated by setting the User-password, access to the data will be blocked only after the system is rebooted by turning off the power, i.e. for the password to take effect, you must turn off and then turn on the computer.
An interesting command related to disk security is SECURITY FREEZE LOCK. Executing this command puts the disk in the FROZEN state and disallows changing passwords until the system is rebooted. The main purpose of this command is to protect the set passwords from unauthorized attacks on the security system, for example, from viruses.
An idea of what commands are executed by the HDD when operating in various security modes is given by table 2, in which the "+" sign denotes the commands being executed. "No" in the cells of the table indicates that the execution of this command in this mode is blocked, and the "***" marks the commands, permission for the execution of which is carried out at the discretion of the HDD manufacturer.
Table 2.
|
Team |
Disk status |
||
|
LOCK |
UNLOCK |
FROZEN |
|
|
CFA ERASE SECTORS |
not |
||
|
CFA REQUEST EXTENDED ERROR CODE |
|||
|
CFA TRANSLATE SECTOR |
|||
|
CFA WRITE MULTIPLE WITHOUT ERASE |
not |
||
|
CFA WRITE SECTORS WITHOUT ERASE |
not |
||
|
CHECK MEDIA CARD TYPE |
not |
||
|
CHECK POWER MODE |
|||
|
CONFIGURE STREAM |
not |
||
|
DEVICE CONFIGURATION |
not |
||
|
DEVICE RESET |
|||
|
DOWNLOAD MICROCODE |
|||
|
EXECUTE DEVICE DIAGNOSTIC |
|||
|
FLUSH CACHE |
not |
||
|
FLUSH CACHE EXT |
not |
||
|
GET MEDIA STATUS |
not |
||
|
IDENTIFY DEVICE |
|||
|
IDENTIFY PACKET DEVICE |
|||
|
IDLE |
|||
|
IDLE IMMEDIATE |
|||
|
MEDIA EJECT |
not |
||
|
MEDIA LOCK |
not |
||
|
MEDIA UNLOCK |
not |
||
|
PACKET |
not |
||
|
READ BUFFER |
|||
|
READ DMA |
not |
||
|
READ DMA EXT |
not |
||
|
READ DMA QUEUED |
not |
||
|
READ DMA QUEUED EXT |
not |
||
|
READ LOG EXT |
not |
||
|
READ MULTIPLE |
not |
||
|
READ MULTIPLE EXT |
not |
||
|
READ NATIVE MAX ADDRESS |
|||
|
READ NATIVE MAX ADDRESS EXT |
|||
|
READ SECTOR (S) |
not |
||
|
READ SECTOR (S) EXT |
not |
||
|
READ STREAM DMA EXT |
not |
||
|
READ STREAM EXT |
not |
||
|
READ VERIFY SECTOR (S) |
not |
||
|
READ VERIFY SECTOR EXT |
not |
||
|
SECURITY DISABLE PASSWORD |
not |
not |
|
|
SECURITY ERASE PREPARE |
not |
||
|
SECURITY ERASE UNIT |
not |
||
|
SECURITY FREEZE LOCK |
not |
||
|
SECURITY SET PASSWORD |
not |
not |
|
|
SECURITY UNLOCK |
not |
||
|
SERVICE |
not |
||
|
SET FEATURES |
|||
|
SET MAX ADDRESS |
not |
||
|
SET MAX ADDRESS EXT |
not |
||
|
SET MAX SET PASSWORD |
not |
||
|
SET MAX LOCK |
not |
||
|
SET MAX FREEZE LOCK |
not |
||
|
SET MAX UNLOCK |
not |
||
|
SET MULTIPLE MODE |
|||
|
SLEEP |
|||
|
SMART DISABLE OPERATIONS |
|||
|
SMART ENABLE / DISABLE AUTOSAVE |
|||
|
SMART ENABLE OPERATIONS |
|||
|
SMART EXECUTE OFF-LINE IMMEDIATE |
|||
|
SMART READ DATA |
|||
|
SMART READ LOG |
|||
|
SMART RETURN STATUS |
|||
|
SMART WRITE LOG |
|||
|
STANDBY |
|||
|
STANDBY IMMEDIATE |
|||
|
WRITE BUFFER |
|||
|
WRITE DMA |
not |
||
|
WRITE DMA EXT |
not |
||
|
WRITE DMA FUA EXT |
not |
||
|
WRITE DMA QUEUED |
not |
||
|
WRITE DMA QUEUED EXT |
not |
||
|
WRITE DMA QUEUED FUA EXT |
not |
||
|
WRITE LOG EXT |
not |
||
|
WRITE MULTIPLE |
not |
||
|
WRITE MULTIPLE EXT |
not |
||
|
WRITE MULTIPLE FUA EXT |
not |
||
|
WRITE SECTOR (S) |
not |
||
|
WRITE SECTOR (S) EXT |
not |
||
|
WRITE STREAM DMA EXT |
not |
||
|
WRITE STREAM EXT |
not |
||

Fig. 2
The difference in the overall sequence of functioning of a disk with an installed and non-installed security system is demonstrated by fig. 2. Moreover, fig. 3 gives an idea of the peculiarities of the functioning of a disk drive when using the security system on the example of IBM disks.

Fig. 3
When guessing an unknown password, remember about such a security feature as limiting the number of attempts to enter a password. This function is also spelled out in the ATA / ATAPI standards and its essence boils down to the following. The disk device must be equipped with a try limit counter. The purpose of this counter is to prevent repeated guessing attempts. The counter value is decremented (decremented by one) at each error in entering the User-password or Master-password. If the counter reaches zero, the disk interrupts the execution of the password commands (SECURITY ERASE UNIT and SECURITY UNLOCK commands) until the disk is turned off or until a hard reset is completed. The initial value of the counter is 5, i.e. after five unsuccessful attempts to guess the password, the system "freezes" and you have to restart your computer. After rebooting the system, the counter is set back to 5.
The state of the attempts counter is indicated in the identification block - a word with address 128 (bit 4, called EXPIRE - see Table 1). If this bit is set to logic 1, it means that the counter has reset to zero, i.e. there have already been 5 incorrect password attempts. After a system reset, bit 4 of word 128 returns to logic 0 again until the next five incorrect attempts. The limit of 5 attempts corresponds only to the User password, and is absent if the Master password is used to unlock the disk.
The ATA / ATAPI standards provide seven security states (SEC0 - SEC6). The transition of a disk from one state to another is carried out when an event occurs (command input, power on / off, system reset). All these seven states and conditions for the drive's transition from one state to another are presented on fig. 4.

Fig. four
This concludes the review of the theoretical foundations of the disk security system, and move on to the practical aspects of using disk passwords.
Setting / removing passwords can be carried out by various specialized utilities, for example, such as:
- ATA Security Tool;
- ATAPWD;
- HDD Unlock Wizard;
- Victoria;
- VTOOL, etc.
Laptops usually have built-in password utilities. In addition, to set and remove passwords, one can use hardware and software systems, one of which is, for example, PC-3000.
When removing the password, it is advisable to use the same program with which this password was set, since otherwise a situation may arise when the correctly entered password (from the user's point of view) is not accepted by the drive. However, in fairness, it should be noted that such a situation may arise even when the same program is used to set and remove a password. And this phenomenon can be offered several explanations.
First, one of the most common reasons that a drive that is password protected by one program cannot be opened by another is the use of different placeholder characters by programs. The USER password consists of 32 characters. In this form, it is fed into the drive and stored in it. When the user sets the password, he can choose any of its length, but 32 bytes are always transferred to the hard drive - these are the characters entered from the keyboard, plus the required number of filler bytes. Usually they are a zero byte (00h code) or a space character (20h code), less often another value (for example, FFh code).
The user of the ransomware program may not know which placeholder the program is using. Therefore, when you enter the same password through another program, placeholders will also be transferred to the drive, but different ones, and the hard drive will give an error (incorrect password). Based on this, it is reasonable to assume that the most correct solution would be to enter all 32 characters, if the usual method does not help. In such well-known programs as Victoria and MHDD, the password is automatically padded with zeros. At the same time, HDDL padding the password with spaces.
Second, an encrypted password can be used. Sometimes there is a situation when the password installer program transmits characters not typed from the keyboard to the hard drive, but their combination encrypted according to a certain algorithm. This is done to exclude unlocking the hard drive by other programs (usually this method is used to protect information in portable devices). There are a huge number of encryption algorithms - these are permutations of symbols in places, and arithmetic-logical conversions (shifts, bit rotation, operations such as XOR and AND, addition with a constant, etc.). In this case, the user usually does not know anything about the fact that the password entered by him is encrypted. To unlock such a hard drive, you must use the tool with which the password was set.
As we noted in the first part of our article, in some cases you can unlock a drive using a Master password, so a service technician should, if possible, know these Master passwords, or be able to find them on the disk. Some Master passwords are presented in Table 3.
Table 3.
|
Storage devices |
Master-password |
|
Fujitsu |
32 spaces |
|
Fujitsu MPG / MPC / MPD / MPE / MPF Series |
1) Master Information -the password, which is the same for the entire series, is stored in the service module 12 (0 Ch) 2) User Information -the password, which is the same for the entire series, is stored in service module 13 (0 Dh) |
|
Hitachi DK 23 AA / DK 23 BA / DK 23 CA series |
32 spaces |
|
IBM DTTA series |
CED79IJUFNATIT + 18 spaces |
|
IBM DJNA series |
VON89IJUFSUNAJ + 18 spaces |
|
IBM DPTA series |
VON89IJUFSUNAJ + 18 spaces |
|
IBM DTLA series |
RAM00IJUFOTSELET + 16 spaces |
|
Maxtor N 40 P |
Maxtor INIT SECURITY TEST STEP + 1 space (password length 31 characters) |
|
Maxtor 541 D |
Maxtor + 26 spaces |
|
Samsung |
There are three possible combinations: 1) BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB (32 symbol " B") 2) AAAAAAAAAAAAAAAAAAAAAAAAAAAAAA (32 symbol " BUT") 3) (32 characters " t") |
|
Seagate |
Seagate + 25 spaces |
|
Toshiba |
32 spaces |
|
Western digital |
WDCWDCWDCWDCWDCWDCWDCWDCWDCWDCWD |
|
Western Digital xB Series |
The password is located at the end of the second sector on track 2 in clear text |
|
Western Digital 07AA / 272AA / 450AA / 205AA series |
The password is located at the end of the third sector on track 1 in clear text |
|
Note ... In this table, passwords are presented strictly case-sensitive, therefore, when entering passwords, it is necessary to observe exactly the same spelling as indicated in this table. |
|
Sometimes disk utilities can spontaneously set a password if the program terminates incorrectly. Below are the passwords set in certain situations by the most popular disk programs:
1) The MHDD 3.x program, when an internal error occurs, sets a password of 32 letters "A" or 32 letters "B" (capital Latin).
2) The HDDL program sets the password "fuck + 28 spaces" in case of an unsuccessful attempt to quickly erase and in case of other failures and freezes.
3) The HRT complex sets 32 characters with a code of 0. In order to enter such a password in the MHDD, it is enough to press in response to the password request.
This is where we will end. And we wish our readers success in their work with the security system of disk drives, and once again draw attention to the seriousness and responsibility of working with disk passwords.
For a long time I wanted to buy a case or cover for my Seagate STDR1000201, but something always made me postpone the purchase. Apparently the whole point is that I use my disk in 99% of cases at home, so it didn't really need additional protection. Although I was ready to buy anything, if only there was somewhere to put the 2.5 hard drive along with the cable (which I always had lying around somewhere separately from the drive), and the Seagate box, in which everything was previously stored, was finally thrown away as unnecessary. And recently, a unique opportunity has turned up to take the product I need almost for free.
So, the review will focus on the case (or bag, as indicated on the product page) Qicent dsp-f3, but exactly the same-looking products can be found under other brands or without any inscriptions on the front part at all. Here is one of the cheapest options: However, I don’t presume that the quality of these products is the same as that of the hero of my review.
Product description.
The product is packed in a transparent bag, inside which, in addition to the case, there was also a cardboard box with inscriptions on which the product model and information about the manufacturing company are indicated.
I ordered a blue case, but there is also a black version on sale, which may have its own characteristics.


Case dimensions:
Weight - 63 grams.
EVA (ethylene vinyl acetate), which is a composite polymer material, was used to make the case.
The inner material is “cotton”, which I cannot translate otherwise than cotton. 


The zipper is made of some kind of alloy and is not steel. In general, no iron is used anywhere in the case, since the magnets that I used to test do not react to anything. 
The zipper does not stick when opening and closing, and in general, the quality of the case pleased me. The threads do not stick out, and there are no irregularities.  - although I only noticed a piece of black material in the center when looking at a photo taken with a flash. This is difficult to see in normal use.
- although I only noticed a piece of black material in the center when looking at a photo taken with a flash. This is difficult to see in normal use.
The strap on the case is non-removable - its length was enough for me to thread my fingers, and wearing it on the wrist is out of the question. 

On the outside of the blue case, there are greasy fingerprints or something else, although most often the stains are quickly rubbed off. It was not for nothing that I mentioned that not only fingers can leave marks, as I accidentally left a stain from the nose on the front part, sniffing at the smell emanating from the case :)
Thus, I smoothly got to the second problem of the Qicent dsp-f3 - it is not a very pleasant smell, which can be felt both from the inside of the case and from the outside. Over time, the smell gradually disappears, or you just get used to it. After reading some articles, I realized that chemical odor is a frequent occurrence for EVA. It's good at least that the smell is felt only in the immediate vicinity.
Inside the case, there is a mesh on one half, and an elastic band on the other, which allows you to store not only the disc, but also various accessories. However, it is not necessary to use dsp-f3 to protect exactly hard drives, as it does not have to be something from the world of technology. If you focus on the pictures that are present on the product page, then the disk should be under the rubber band, and the cable under the net, but I did the opposite. Due to its small size, the disc cannot be reliably pressed with an elastic band, so you need to put something under it or, on the contrary, put it on top. 






Kingston mobilelite wireless g2 is more suitable for the case: 
On the product page, water resistance is indicated, but, obviously, it meant protection from splashes, since water easily penetrates into the case through the fastener. But the solid blue material really does not let water through.
After water procedures: 
The seller also claims anti-corrosion, anti-static and dust-proof properties. I can only write that the sand definitely does not go inside.
Bottom line.
The Qicent dsp-f3 is quite suitable for carrying various objects and will certainly provide some protection in the event of falls. Although it is better not to drop hard drives at all, even if they are in a case. Another point is that there are many similar products on Aliexpress and dsp-f3 is not the cheapest of them, but I want to believe that it is better than its more budget counterparts. However, there was a time when the reviewed case cost $ 2, which is 99 cents less than today's price (06/13/2017). On the other hand, the seller often has $ 1 coupons that can be exchanged for coins.
HDD- one of the most important components computer system, it is he who is responsible for the long-term preservation of important, and not very information. Therefore, special attention should be paid to protecting the hard drive from software failures and mechanical damage, because only protection will preserve and prolong its performance.
A hard disk is a complex electronic-mechanical structure. If we consider the device of a hard disk in a simplified way, it turns out that it consists of three main units: magnetic disks, magnetic read-out heads and a control microcircuit. If at least one of these nodes fails, the entire hard drive will break down, and, consequently, data loss. In contrast, the usual one is more reliable, but less transportable.
To prevent these and many other problems from happening, you must follow the basic rules for protecting your hard drive.

- It is necessary to observe the temperature regime. Too high or low temperature has a great impact on the performance of the hard disk, because the temperature changes the microgeometric parameters of the hard disk platters. Therefore, you should not exceed the upper limit of the operating temperature of the hard disk. Typically, the operating temperature range is 55-60 ° C.
- Ensure that there is sufficient distance between the hard disk and the chassis for free air circulation, because the hard disk is a passively cooled device. In this case, you should not place hard drives close to each other, or next to a video card, optical drives, or other elements that actively generate heat. Also, pay attention to the fact that the contact area of the hard drive with various metal elements of the case must be large enough to dissipate heat to the case. And if you still want to install a device for active cooling of the hard drive, prepare for this issue very carefully and carefully. Because the fan installed on the hard drive can create vibration, which is just as harmful to the operation of the drive as heat: with increased vibration, the time to find the desired track increases, which leads to an increase in the load on all nodes of the hard drive, and this significantly reduces the life of the hard drive.

- Protect the hard drive from shock and shock. Because just one blow to the hard drive can lead to a deviation of the head from the desired position, as a result of which the so-called head pop occurs: when the head returns to its original position, it strikes the disk surface and damages the ferromagnetic coating.
- It is necessary to protect the hard disk from power surges. Because a sharp increase in voltage can cause a sharp increase in the temperature of the hard drive elements, which can lead to overheating of the control microcircuit. Therefore, it is necessary to take care of supplying the computer system with an uninterruptible power supply, which will perfectly insure the computer in case of an unexpected power outage, it is necessary in advance.
But, of course, even with strict adherence to all the rules of protection and precautions, it will not always be possible to protect the hard drive from new malfunctions, which may be associated with an incorrect selection of the computer configuration, or with poor-quality parts, or with too high load on the system. Therefore, always remember to back up data to third-party drives in order to insure yourself as much as possible against the loss of important data.
Take good care of your equipment and it will help you walk around the open spaces without any problems.